Category: Security
Poor DR Planning = Business Downtime

Ask a roomful of CIOs what keeps them up at night, and data disruptions and downtime are sure to be near the top of the list. And for good reasons: a study by consulting firm ITIC found that 40% of large enterprises estimated the hourly cost of downtime at over $1 million.
A good disaster recovery plan can help minimize disruptions and maximize business continuity in these situations, but these DR plans need to be tested and maintained regularly.
The fast-pace of innovation across the IT industry accelerates the lifespan of technology and best practices. What was considered state-of-the-art last year, just might be a vulnerability this year. One survey found that 29% of organizations with a disaster recovery plan test it just once a year, and 23% never test it at all.
Data recovery plans have many components, and identifying potential exposure or shortfalls can be a challenge for even the most seasoned IT team.
10 Questions to Ask About Your Current Disaster Recovery Plan
- What are your data restoration targets? Depending on your backup infrastructure, retrieving your data could take as little as one hour — or as much as several days. Setting your recovery targets involves several considerations, such as the cost of downtime to your business, the long-term impacts on your reputation and brand, and the costs of establishing and maintaining your DR infrastructure.
- Where are you backing up your data? Options for backup range from cloud providers to specialized services that replicate your complete environment in an offsite data center. In the event of a hurricane, retrieving your data from cloud providers like AWS may take considerable time, especially if your network and computing infrastructures have been damaged. Some specialist providers will replicate your full hardware, software, and data infrastructure onsite, speeding the retrieval process.
- How often are you performing backups? Backup frequency can depend on the volume and criticality of your data, the cost of data backup, and the ability of your infrastructure to complete backups without impacting your business. For organizations with outdated network infrastructures, frequent or real-time backups can slow network performance to a crawl.
- What is your hardware replacement strategy? While a robust data backup plan is critical, it’s only part of the picture. A data disaster can wipe out servers, storage, and other essential hardware components. The ability to quickly replicate your hardware infrastructure is a major factor in how quickly you can recover from a major storm or other natural disaster.
- How often do you test your disaster recovery plan? While disaster recovery testing takes up considerable time and resources, regular testing will ensure plan viability and help identify potential shortfalls. Outsourcing disaster recovery planning can relieve the internal resource burden for many companies.
- How secure is your data? Data should be encrypted in transit, and offsite storage providers should employ state-of-the-art physical and cybersecurity infrastructures.
- Do you have in-house expertise? Developing and maintaining disaster recovery protocols can require specialized in-house resources and represent a considerable investment in team bandwidth. That’s one reason why many organizations opt to outsource disaster recovery planning and execution.
- What if you switch backup suppliers? How easy is it to repatriate your data if you choose to move to a new backup and storage supplier? It’s critical to maintain control of your data and know you can easily migrate it if necessary.
- Are you employing best-in-class hardware and software? Disaster recovery solutions are quickly evolving to deliver faster and more reliable, cost-effective performance. You should evaluate your infrastructure regularly to ensure you and your providers are leveraging the best available solutions and following established recovery best practices.
- Is your disaster recovery plan cost-optimized? Encrypting, transporting, and storing data is not cheap. An optimized solution will help maintain or even reduce your ongoing operational costs.
The Data Protection Audit — A Smart First Step
Finally, organizations should consider beginning with a third-party data protection audit to assess their current disaster recovery readiness. Specialized providers have the tools, expertise, and experience to identify shortfalls and recommend appropriate remedial actions.
A data protection audit will help your organization to:
- Validate your business goals and establish recovery point and time objectives
- Review the effectiveness of your existing backup solution
- Assess your security posture and ransomware detection capabilities
- Evaluate your hardware and storage infrastructure
- Provide prioritized recommendations based on security, backup, and disaster recovery best practices
Schedule your data protection audit – no strings attached. The audit is done by our data recovery experts and takes 30-minutes or less of your time. Trade thirty minutes of your time to avoid sleepless nights worrying about your data.
__________
Path Forward IT offers a free Data Protection Audit that will evaluate your current disaster recovery capabilities and recommend the best ways to optimize your data security and recovery solution. Find out more here.
What Most People Don’t Know About Cyber Insurance

As cyberattacks grow in frequency and severity, the demand for cyber insurance is exploding in response. According to Fortune Business Insights, the 2021 cyber insurance market was valued at an estimated $7.60 billion in 2020 and projected to grow to $36.85 billion by 2028 — a CAGR of 25.3%. Zurich America estimated that by 2020, 78% of large organizations had purchased cyber insurance coverage of some type.
While insurance can help defray the costs of recovering compromised data and restoring damaged computers and storage devices, networks must be kept compliant with the terms of the policy. Otherwise, in the event of a cyberattack, your claim may be delayed or even denied. Keeping your environment in compliance can represent significant, ongoing costs to your organization — but the cost of neglecting compliance can be much higher.
What Is Cyber Insurance?
A cyber insurance policy (also referred to as ‘cyber risk insurance’ or ‘cyber liability insurance coverage’) is a financial product that enables businesses to transfer the costs involved with recovery from a cyber-related security breach or similar events. Typically, the most important aspect of cyber insurance will be network security coverage. This will offer coverage in the event of a network security failure – such as data breaches, malware, ransomware attacks, and business account and email compromises. However, the policy will also respond to liability claims and ancillary expenses of an attack or breach.
Learn more about data protection services.
Coverage and Benefits
While cyber insurance coverage varies from provider to provider, typical policies cover organizations in five key areas:
Lost data. Companies are legally responsible for their data, whether stored locally, offsite, or in the cloud. And, if personal information (like protected health records) is exposed, companies may be liable. Cyber insurance typically covers the cost of recovering compromised data, notifying impacted customers, and may cover legal defense expenses.
Lost devices. Stolen or compromised laptops and mobile devices are a leading cause of compromised data. Many cyber insurance policies provide information liability coverage that covers the cost of device replacement, plus legal and other expenses.
Customer notification. The cost of notifying customers and impacted parties about a breach and ongoing remediation efforts can be significant. Cyber insurance can help compensate for the costs of legal counsel and specialized communications providers.
Investigation and forensics. Computer forensics experts help assess the extent of a cyberattack and determine whether sensitive data has been compromised. Cyber insurance may reimburse organizations for the cost of those expert services.
Miscellaneous expenses. Insurance may also help offset the cost of lost business, restoring compromised systems, and other expenses incurred during business restoration.
Tips to Ensure Compliance with Your
Cyber insurance is relatively new in the market, and many providers lack the historical data to accurately assess their risks. As a result, policies often require customers to maintain high security compliance standards to qualify for payouts in the event of a breach. Organizations relying on cyber insurance to compensate for inadequate security practices may be in for a shock when they make a claim, especially if they haven’t read the fine print in their cyber insurance contracts.
While the definition of compliance can vary from provider to provider, certain security best practice requirements are common to most policies and should be prioritized:
Third-party audits. An external security audit will help identify potential security issues and can help establish a detailed remediation plan.
Comprehensive backup and recovery plans. Effective backups are one of the best defenses against cyberattacks. Secure, regularly-tested, cloud-based backups will replicate data offsite and help minimize downtime resulting from a breach.
Regular penetration testing. Penetration testing (completed annually at a minimum) can also uncover security gaps while helping to reduce risk from the insurer’s perspective.
Effective password controls. Some policies will insist on adherence to password best practices as a policy condition. These best practices include using strong passwords (letters, numbers, and symbol combinations), different passwords for every service, and even two-factor identification.
Comprehensive data encryption. All sensitive data must be encrypted at rest or in transit. Data access (physical or online) should be highly regulated.
Beyond Compliance: Expert Tips
While your policy will help define your cybersecurity priorities, here are two other steps you can take to strengthen your security infrastructure and minimize any issues if you need to make a claim.
Security training. Onboarding training for new hires and regular refreshers for existing employees will reinforce your organization’s security practices, create a ‘security-first’ culture, and help minimize unintentional breaches and exposure.
Collaborate with your insurance provider. A regular dialogue with your insurer allows you to communicate your ongoing security initiatives, identify and resolve any issues, and explore ways to enhance your coverage and optimize your insurance costs.
The Value of an Expert Security Partner
A security-focused integrator can help optimize your organization’s security infrastructure and best practices to ensure you’re compliant with the terms of your cyber insurance policy.
At Path Forward IT, we’re experts in security and compliance. For years we’ve helped healthcare leaders meet stringent HIPAA, HITECH, and CMS requirements, and we bring the same knowledge and expertise to our customers in finance, education, and other industries.
Path Forward IT can work with your team to ensure cyber insurance policy compliance by conducting third-party audits and penetration testing, identifying and remediating security gaps, implementing operational best practices, and providing ongoing security training.
Contact us to learn how we can help you ensure compliance with your cyber insurance policy.
How a Backup and Recovery Audit Can Safeguard Your Business

Are you part of the 72% of organizations that don’t have an adequate data recovery (DR) plan in place? Even if you’ve maximized your resources to protect your data, your organization may not be fully prepared. A backup and recovery audit assesses your data security and DR readiness and provides valuable intelligence to ensure you have the right plan in place.
Your Data Is at Risk
Data is more vulnerable than ever. It is critical to frequently assess that your posture is keeping pace with the latest threats; however, there is no guaranteed way to stop a determined criminal.
Cybercriminals are relentless in their efforts to breach businesses, sabotage data, or hold it for ransom. A solid data recovery plan creates another viable alternative to paying an enormous ransom.
Cybercriminals aren’t the only threats to data — Mother Nature can wreak havoc too. The effects of too much (or not enough) rain can result in extreme flooding conditions for some and wildfires for others. There’s only a small window of warning when it comes to hurricanes and tornadoes, and with safety as the first priority, worrying about data loss only adds extra stress.
Knowing how, when, and which data can be restored in the event of a data disaster is critical information for any business. That alone is enough reason to conduct a data recovery audit to confirm the viability of your plan; however, there are other benefits. Here’s how you can use a backup and recovery audit to inform your business strategy.
>>Is your data recovery plan ready to withstand Mother Nature? Find out.
Re-evaluate and Re-Prioritize IT Budgets
As your business evolves, so should your data protection plan. Budgetary allocations often don’t consider changing needs or emerging (and better) technologies, especially in the case of data storage and security.
A backup and recovery audit provides ‘proof points’ to help drive budget changes or reallocations to keep pace with cybersecurity and right-size your data backup and DR initiatives.
IT executives need to consider two important factors when allocating resources for DR: compliance requirements and the cost of downtime. Many organizations’ backup and DR needs are driven in part by their industry compliance requirements. This is especially true for financial institutions, government, and healthcare entities who must adhere to standards like FDIC, SSAE, HIPAA, and GDPR. As these standards evolve, organizations must review and enhance their DR capabilities to keep pace.
To determine the appropriate backup and disaster recovery investments, organizations should first calculate their specific downtime costs. These include lost revenues and productivity, recovery expenses, and intangibles (e.g., lost future business, damage to reputation).
Downtime costs add up quickly, especially in the face of a natural disaster. For example, Hurricane Rita resulted in 384 hours of power outages, and Hurricane Sandy caused 337 hours. According to a 2021 survey by ITIC, 44% of enterprises say downtime costs can exceed $1 million per hour.
Armed with the backup and recovery audit findings, a summary of compliance requirements, and an understanding of downtime costs, business leaders can make informed decisions about resource allocation to address data backup requirements.
>>Schedule your third-party data protection audit with Path Forward IT, no strings attached.
Optimize Network Infrastructure and Performance
A backup and recovery audit does more than uncover misalignments between your business-driven backup and recovery requirements and your existing DR plan. It also helps identify and resolve network infrastructure and performance issues that prevent your backup and DR plan from working properly.
Frequent backups drive significant network traffic, and the strain on legacy networks may impact the performance of other critical applications. If the audit identifies network performance issues, it allows the IT department to see any vulnerabilities in traffic flow, areas to improve network performance, and key components of backup and recovery plans. Executing audit recommendations will lead to smoother day-to-day operations and greater productivity for the IT department and the entire company.
>>Learn more about what is covered in a backup and recovery audit.
Internal Versus Third-Party Audits
After understanding the value of a data recovery audit, the next step is to ensure the quality of the audit. Engaging a third-party vendor is almost always the best option. For the same reasons accountants trust a third-party auditor to confirm a company’s financials, IT teams benefit from an outsider perspective to take a fresh look and validate its data protection strategy.
The audit’s goal is not to ‘call out’ the internal IT team or their hard work. A third party brings an outsider perspective, the benefits of having conducted hundreds of previous audits, and the ability to work with the internal team to ensure the business data recovery plan will perform as expected.
Contact Path Forward IT to schedule your data audit today and learn how our DR experts can give you crucial insights into your business continuity plan.
Is Your Data Recovery Plan Hurricane-Ready?
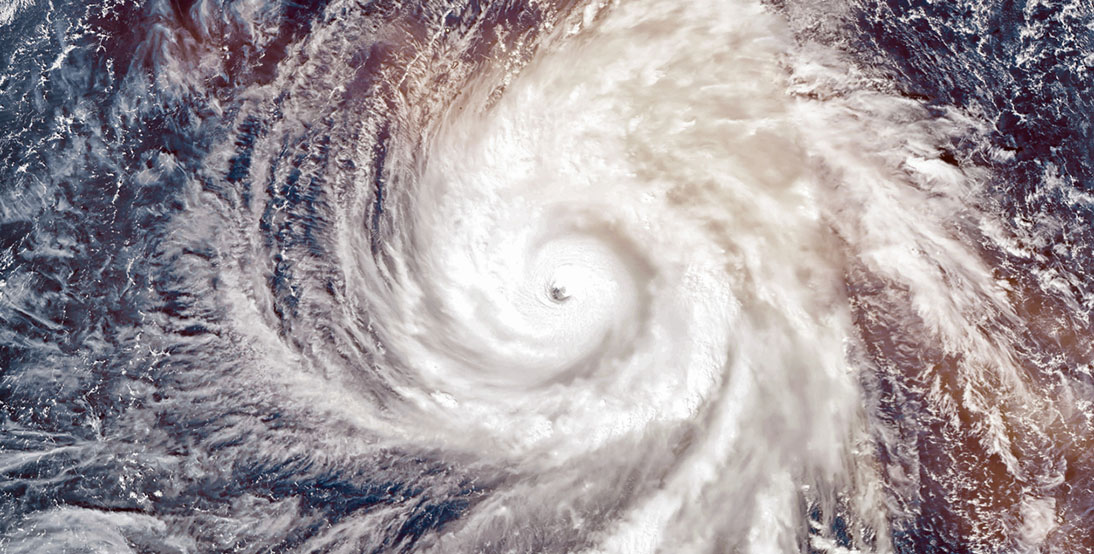
Ask a roomful of CIOs what keeps them up at night, and data disruptions and downtime are sure to be near the top of the list. And for good reasons: a study by consulting firm ITIC found that 40% of large enterprises estimated the hourly cost of downtime at over $1 million.
While network disruptions caused by cyberattacks and data breaches capture most of the headlines, natural disasters can have significant — or even fatal — consequences for many organizations. For businesses operating in the southern and eastern regions of the US, hurricanes can represent the greatest risk of all.
Hurricane Frequency and Severity Are on the Rise
In 2020, 11 hurricanes made landfall in the US, breaking the previous record of nine in 1916. While growing in frequency, hurricanes are also causing more destruction — more than $51 billion in 2020.
Major storms can impact businesses in many ways — taking networks down, causing data loss, destroying infrastructure, and restricting employees’ ability to work. Remediation efforts can take significant time and resources and are not always successful. FEMA estimates that 9 out of 10 small businesses fail if they cannot resume operations within five days after a disaster.
Despite those dire consequences, Gartner estimates that 72% of organizations do not have adequate disaster recovery or data protection capabilities. Another survey found that 29% of organizations with a data recovery plan test it just once a year, and 23% never test it at all.
Don’t wait: Sign up for your free data protection audit.
10 Questions to Ask About Your Current Data Recovery Plan
Data recovery plans have many components, and identifying potential exposure or shortfalls can be a challenge for even the most seasoned IT team.
Here are ten areas to consider when evaluating your plan:
- What are your data restoration targets? Depending on your backup infrastructure, retrieving your data could take as little as one hour — or as much as several days. Setting your recovery targets involves several considerations, such as the cost of downtime to your business, the long-term impacts on your reputation and brand, and the costs of establishing and maintaining your DR infrastructure.
- Where are you backing up your data? Options for backup range from cloud providers to specialized services that replicate your complete environment in an offsite data center. In the event of a hurricane, retrieving your data from cloud providers like AWS may take considerable time, especially if your network and computing infrastructures have been damaged. Some specialist providers will replicate your full hardware, software, and data infrastructure onsite, speeding the retrieval process.
- How often are you performing backups? Backup frequency can depend on the volume and criticality of your data, the cost of data backup, and the ability of your infrastructure to complete backups without impacting your business. For organizations with outdated network infrastructures, frequent or real-time backups can slow network performance to a crawl.
- What is your hardware replacement strategy? While a robust data backup plan is critical, it’s only part of the picture. A hurricane can wipe out servers, storage, and other essential hardware components. The ability to quickly replicate your hardware infrastructure is a major factor in how quickly you can recover from a major storm or other natural disaster.
- How often do you test your disaster recovery plan? While disaster recovery testing takes up considerable time and resources, regular testing will ensure plan viability and help identify potential shortfalls. Outsourcing disaster recovery planning can relieve the internal resource burden for many companies.
- How secure is your data? Data should be encrypted in transit, and offsite storage providers should employ state-of-the-art physical and cybersecurity infrastructures.
- Do you have in-house expertise? Developing and maintaining disaster recovery protocols can require specialized in-house resources and represent a considerable investment in team bandwidth. That’s one reason why many organizations opt to outsource disaster recovery planning and execution.
- What if you switch backup suppliers? How easy is it to repatriate your data if you choose to move to a new backup and storage supplier? It’s critical to maintain control of your data and know you can easily migrate it if necessary.
- Are you employing best-in-class hardware and software? Disaster recovery solutions are quickly evolving to deliver faster and more reliable, cost-effective performance. You should evaluate your infrastructure regularly to ensure you and your providers are leveraging the best available solutions and following established recovery best practices.
- Is your disaster recovery plan cost-optimized? Encrypting, transporting, and storing data is not cheap. An optimized solution will help maintain or even reduce your ongoing operational costs.
The Data Protection Audit — A Smart First Step
Finally, organizations should consider beginning with a third-party data protection audit to assess their current disaster recovery readiness. Specialized providers have the tools, expertise, and experience to identify shortfalls and recommend appropriate remedial actions.
A data protection audit will help your organization to:
- Validate your business goals and establish recovery point and time objectives
- Review the effectiveness of your existing backup solution
- Assess your security posture and ransomware detection capabilities
- Evaluate your hardware and storage infrastructure
- Provide prioritized recommendations based on security, backup, and disaster recovery best practices
Schedule your data protection audit – no strings attached. The audit is done by our data recovery experts and takes 30-minutes or less of your time. Trade thirty minutes of your time to avoid sleepless nights worrying about your data.
Don’t Wait For Hurricane Season
Optimizing your data recovery plan takes time. It can involve allocating budgets and resources, procuring hardware and software, updating processes, and establishing new service provider relationships. If your company is located in areas impacted by hurricanes, you can’t afford to wait until hurricane season to evaluate your disaster recovery plans — you should begin now.
Are you ready for the next Harvey, Sandy, or Katrina?
__________
Path Forward IT offers a free Data Protection Audit that will evaluate your current disaster recovery capabilities and recommend the best ways to optimize your data security and recovery solution. Find out more here.
Cybersecurity First: Cyber Literacy Protects Your Valuables

Each year in October, security professionals, educators, computer enthusiasts and others support Cybersecurity Awareness Month—co-led by the Cybersecurity and Infrastructure Security Agency (CISA) and the National Cyber Security Alliance (NCSA)—by raising awareness about the importance of cybersecurity. Weekly themes give businesses and organizations an opportunity to geek out, err, explain concepts like the layered security model, phishing scams, ransomware, the importance of data backups and so much more. The theme for the final week in October 2021 is cybersecurity first.
It’s Not What You Think
When we talk about, “cybersecurity first,” most think it means cyber threat preparedness, awareness, prioritization or some variation of that (and a cybersecurity-first mindset will definitely get you further down the secured technology road than the set-it-and-forget-it crowd.) But what we’re really talking about is much more foundational to ensuring we can continue to address complex cybersecurity challenges today and well into the future. We’re referring to cyber literacy—a baseline cyber proficiency that doesn’t really exist among non-cyber professionals but should.
We take a collective run at educating businesses and consumers about evolving cyber threats, rapidly-expanding technologies, and the seriousness of our growing dependency upon them as mission-critical functions are increasingly connected to global networks. There’s much to learn and do to adjust our current technical and operational environments to accommodate our changing physical ones.
Fundamentally Secure
Faced with addressing the challenge of safeguarding the work-anywhere remote workforce has caused security professionals to rethink IT fundamentals, noting blind spots, lack of visibility, legacy system vulnerabilities and outdated security strategies. While there isn’t a single technology that will stop every threat, you can, and should, make it as difficult as possible for attackers to penetrate your environment. An attacker may be targeting multiple victims simultaneously to locate the most easily accessible opportunities so, the more barriers in his path, the more likely he may decide it takes too much effort to infiltrate your organization.
A First Line of Defense
A next-gen firewall (NGFW) is a fundamental, and indispensable, frontline defense that sets up a perimeter against harmful network traffic. A NG firewall combines a traditional firewall with other network device filtering functions, such as an application firewall, using in-line deep packet inspection (DPI), that goes beyond simple port and protocol inspection by inspecting data carried in network packets.
With Big Data driving more efficient operations, innovation, and customer insights, enterprise cloud-based storage is now a necessity instead of an option. A vast majority of enterprise firewalls don’t protect cloud storage systems, as it’s not part of the internal network. But the Palo Alto Networks firewall creates a virtualized network that also includes cloud storage, using site-to-site VPN tunnels, to ensure reliable protection of sensitive data stored in the cloud. Palo Alto Networks is a preferred vendor for smaller enterprises for this very reason—it’s an ideal firewall for protecting networks using cloud-based file-sharing services like Apple iCloud, Google Drive, or Dropbox.
Part of a Greater Plan
Though a NG firewall can’t provide 100% protection, it is an important part of the network security mix. Multiple IT teams count on the firewall to enable them to do their jobs effectively and efficiently, for varied reasons:
- Networking teams prioritize hassle-free integration with existing architecture, ease of deployment and use, and network performance and uptime.
- Security teams focus on seamless integration with security controls, better overall security, and threat prevention.
- Security operations teams work best with single-pane management and automation for security features and capabilities.
- Data center teams need automated features and capabilities, segmentation of hybrid cloud environments, scalability to meet changing needs, and single-pane management.
- Application teams value simple, fast, and secure application development and deployment.
Next-Level Integrations
Blumira’s modern cloud Security Information and Event Management (SIEM) platform integrates with Palo Alto Network’s next-gen firewalls to detect cybersecurity threats, automating actionable alerts to remediate when a threat is detected. When Blumira’s dynamic blocklist capabilities are configured to work with Palo Alto Network firewalls, Blumira provides automated blocking of known threats, automatically adding new block rules when threats are detected.
Worth the Risk?
With so much media attention on cyber exploits, it’s easy to question whether the rewards of technological advancements outweigh the risks. Cybersecurity as a priority continues to be compared and weighed against competing business interests and is often deprioritized as a nice-to-have.
When we consider lifestyle-defining technologies like alternating current, semiconductors, logistics systems, automation, fiber optics, telecommunications, and more—that have resulted in modern marvels like medical centers, manufacturing, transportation systems, Apollo guidance computers… we have to wonder if we’d be where we are if creators had thought of protecting their inventions as a cost center versus an investment. Logic says, risk should naturally accompany innovation, but should there be a question about protecting what’s already been created?
It really comes down to the value you place on what you seek to protect.
Let Path Forward IT help optimize your firewall management to protect valuable data and assets by:
- Segmenting your network to ease Big Data monitoring; boost performance; localize technical issues and—most importantly—enhance security
- Upgrading your legacy firewall to ensure sensitive data protection in cloud storage too
- Right-sizing your next-gen firewall solution to best fit your business needs
- Auditing your unique environment and deploying the IT assets that will up-level your perimeter protection and improve overall security posture
Let us help you identify the key security priorities for your unique business.
Resources
What’s Your Perimeter? Network, Identity, or Endpoint?, CISO Mag
VMware Global Security Insights Report
Partner Perspectives: Disrupt Advanced Threats with Blumira + Carbon Black
Cloud SIEM for Palo Alto Next-Gen Firewalls
5 Critical Mistakes When Evaluating a Next Generation Firewall
Operating in the Dark: Cyber Decision-Making from First Principles, Journal of Information Warfare
The Information Security Practice Principles, IU Center for Applied Cybersecurity Research
Combatting Stealthy Cyber Enemies in Today’s Digitally-Accelerated Economy

In early 2021, a cyber-attack was made on a water treatment facility in Oldsmar, Florida. The hacker infiltrated its computer systems and changed settings, increasing the volume of sodium hydroxide, slated to enter the water supply, to an excessive amount. A single, vigilant employee managed to catch the issue before it could do damage.
With all the knowledge and information available today to thwart cyber threats, why does this keep happening to fundamental human lifelines like utilities, healthcare, finance and business?
Is the adoption of new technologies not keeping pace with advanced threats? Are poor access controls, legacy systems, remote access, ransomware and insider threats to blame? Or are businesses just understaffed, under-resourced, and plain overwhelmed by what digital acceleration means for them right now and in the future? The answer for most is likely, D: All of the above.
The Age of Acceleration
The events shaping the past couple of years could easily define the time period as, “The Age of Disruption”, with the Covid-19 pandemic flipping everything about how businesses and communities engage on its head. But one theme that is consistent throughout is acceleration. We are all reimagining, transforming, adopting, adapting and repositioning in some way to engage and connect with others in new and different ways. And, if you—a corporation, small business owner, hardworking citizen, or contributing member of society—are doing that, unfortunately, so are cyber criminals.
You probably don’t typically spend a great deal of time thinking like a hacker. But, under the circumstances, it might be a helpful exercise to do so. What circumstances, you ask? For one, what does disruption or accelerated change mean to a hacker? Again, unfortunately, not much. Stealthy cyber criminals operate flexibly to be in position to exploit windows of opportunity. You probably see where this is going. Not only are we not on an even playing field, but we also don’t have the advantage. Cyber criminals are capitalizing on the transition to remote work, the scramble for businesses to adopt new operating models, and the vulnerability of unsecured or under-secured legacy systems, and there’s more to come.
Digital Accelerants
There’s more pressure than ever before to protect networks as the channel for conducting business in today’s global marketplace. Protecting the network from threats and vulnerabilities can be daunting under normal circumstances but, there are currently several technology disrupters driving digital acceleration that will impact the future of networks. These include AI, machine learning, Big Data and analytics, and 5G. Some are new, some are not, but all are interdependent and add complexity to existing IT systems.
“While digital technologies have been developing for many years, in the last decade their cumulative impacts have become so deep, wide-ranging and fast-changing as to herald the dawn of a new age. The cost of massive computing power has fallen. Billions of people and devices have come online. Digital content now crosses borders in vast volumes, with constant shifts in what is produced and how and where it is used.”—Digital Cooperation Report for the Web
The Evolution of Ransomware
Unassuming ransomware. It targets files in a slow-moving progression, zapping users’ access by restricting files and/or access at the system level. In 2020, research showed a 7-fold increase in ransomware attacks, as compared to 2019. That might not be as concerning if ransomware hadn’t also evolved. The ransomware families that appeared popular in 2019 are no longer as popular now. New ransomware families dominate the scene, and they no longer target individuals, but companies.
The many ways ransomware can spread infection today is quite varied and comprehensive. It might surprise you, the breadth of damage that can be done via an attack on mobile devices, Wifi networks, cloud storage, external hard drives, unpatched operating systems, and backups (yes, even your backups can be hacked). Ransomware can reside in a variety of applications, ranging from Skype to the Google Play Store, and gain systems entry through suspicious emails and fake desktop updates. Once downloaded, malware can hide in modified Windows registry keys, temporary folders, Microsoft Word files and elsewhere. It can even encrypt encrypted files at the device and file levels and hold them hostage for ransom, hence the name.
Ransomware begins simply enough, but like slow-growing cancer, your infected network then metastasizes and progresses to impacting your customers, service providers, utilities, all the way down to employees. So, how do you protect critical information assets traveling across your network?
Don’t Open the Door
Similar to how employee security awareness training helps close the door on social engineering and phishing attacks, application execution control closes the door on unknown threats, like ransomware and malware, while permissions settings “allow” trusted software to run within the IT infrastructure. Application allow-listing (formerly known as whitelisting) technology solutions, such as those offered by cybersecurity leader, ThreatLocker, simplify deployment with semi-automated options that ease the burden of manually building an allow-list.
Read more: 5 Tips for Protecting Data.
The Era of Managing Everything In-House Is Over (at least, for now)
Ransomware is on the rise because it’s underestimated and easy to deploy to vulnerable targets. During a time of unprecedented technological acceleration and economic and societal change, companies don’t have to be unwitting victims.
Right now, while cyber enemies are on the increase, cybersecurity roles are the hardest to fill. There’s something really wrong with that order that will, hopefully, resolve itself over the course of time. But you don’t have to wait till then to get the technical help you need. Whether you have an IT resource, an internal team, or no cybersecurity support at all, MSP, Path Forward IT can be the security partner who helps you confidently establish and implement your allow-listing strategy.
A few other ways Path Forward IT can support you and keep your network safe include:
- Administer security awareness training to your employees, including mock phishing attacks
- Conduct an audit to review your protection, hardware, and security configurations
- Collaborate on policies development, ensuring compliance with HIPAA, NIST, and other industry regulations
- Assure your network security through managed cloud services, including proactive 24/7/365 monitoring, updates, and patching, as well as immediate response in the event of a security breach
To learn more, request a consultation with Path Forward IT.
Resources
IT auditing and controls: A look at application controls, Infosec Institute
Visibility and Control at the Application Layer, ThreatLocker
NIST Guide to Application Whitelisting
The Ransomware Landscape of 2021, Brilliance Security Magazine
What you need to know about ransomware, CyberTalk.org
WannaCry Ransomware Attack, Wikipedia
MalwareTech, WannaCry and Kronos – Understanding the Connections, Tripwire
Your Employees Are the Latest Phishing Targets

With burgeoning hybrid work environments, companies and their employees are more susceptible than ever to phishing attacks and social engineering. Cybercriminals are becoming increasingly more adept at changing tactics to exploit new vulnerabilities. As phishing attempts get more creative and difficult to discern, “new-school” employee training and access controls are a must.
Jumping Phish Ponds
Most of us have heard of phishing or even taken a cybersecurity compliance training that touched upon the threat. We know emails that seem “off” somehow are suspect—an invitation to click on a link from a stranger or a weird request from a usually trustworthy source. Social engineering like this is a cybercriminal’s attempt to manipulate, influence or deceive a target into taking some action that isn’t in their own best interest or in the best interest of the organization.
Phishing scams these days have changed in nature due to a variety of recent developments. During 2020, COVID-19, shelter-in-place and social distancing orders forced many companies to quickly adapt to changing environments and technology. Under these conditions, it wasn’t always possible for network access and privilege escalation to be fully monitored. Misconfigured databases and services were the leading cause behind all-time-high numbers of exposed records in enterprise security breaches. As more automation tools are being implemented on company networks to streamline new operational models, the ability to keep track of who has access to different points on the network, and what type of access they have, is becoming more complex to manage.
New Phish
These recent changes are driving bad actors away from “net” phishing and toward spear phishing (targeting specific groups and individuals.) The FBI’s Internet Crime Complaint Center (IC3) received a record number of complaints from American citizens in 2020. Phishing—including vishing (voice phishing over the phone), SMiShing (text message phishing), whaling (targeting high-profile employees and C-level executives) and pharming (emails with links that redirect to fake websites)—was the most prevalent threat in the US in 2020, with 241,342 victims. This resulted in non-payment/non-delivery (108,869 victims), extortion (76,741 victims), personal data loss (45,330 victims) and identity theft (43,330 victims).
Phishing Victim Impacts
Link manipulation, fake trial offers, advance-fee loans, and job scams continue to be lucrative phishing methods for threat actors. The consequences, however, are high for victims. Here are some numbers shared by Business Continuity and Disaster Recovery MSP, PathForward IT:
- ~85% of security breaches start with phishing
- 86% of organizations had at least one user try to connect to a phishing site
- 53% of successful cyber-attacks infiltrate organizations without being detected
- 91% of all cyber-attack incidents didn’t generate an alert
- 70+ days: Length of time intruders typically go undetected
- 6–12 months: Estimated time to investigate and remediate a security breach
- 3–15 days: Average downtime, interruption to business continuity
- $1M–$3M: Financial impact of a successful attack
- Regulatory, civil, and criminal impacts: Fines, restitution, penalties to contracted partners, and brand reputation damage
Defending Against Phishers
Recognizing and stopping phishing attacks in advance of a data breach or ransomware is your best defense. The following are recommended mitigations that can help prepare and protect your organization:
POLICIES AWARENESS: The greatest threat to your organization’s cybersecurity strength is, unfortunately, also its greatest asset. Even if unintentional, employee carelessness, mistakes, unreported data exposures and other risky behaviors can provide easy entry points for bad actors. Raising awareness about policies that defend against security threats arm your employees with knowledge that can protect them in the workplace and also in their home offices. Here is just a short list of examples your policies should address:
- Verify financial-related request with a live phone conversation before responding
- Avoid clicking links from unknown senders, suspicious-looking or unverified emails asking for payment or banking information
- Never put financial account information in an email, text or other digital communication unless it’s encrypted
- Never use public WiFi to access your company email, financial institutions or any sensitive data
TRAINING: Providing training to your employees improves their ability to recognize threats and reduces the chance of successful phishing attempts. As cyberattack trends change, ongoing, updated training lessens your organization’s exposure and ensures new attack methods don’t catch your employees unaware. Path Forward IT training and documentation programs leverage best-in-class training tools from preferred vendor, KnowBe4, to help your team correctly utilize your technology’s full features and capabilities while meeting regulatory training requirements. Security Awareness Training, Anti-Phishing Training, and simulated phishing attacks can all help your employees gain real-world experience on how to address threats.
ACCESS CONTROLS: When new employees are hired, network access should be granted on a least-privilege scale. Periodic review of network access for all employees can significantly reduce the risk of compromise of vulnerable and/or weak spots within the network. Actively scanning and monitoring for unauthorized access or modifications can help detect a possible compromise in order to prevent or minimize the loss of data.
To learn more, request a consultation with Path Forward IT.
Resources
Internet Crime Complaint Center
50 Phishing Stats You Should Know In 2021
Cyber Criminals Exploit Network Access and Privilege Escalation
The Pandemic Struck, and Cybercriminals Went to Work
Report: 2021 Phishing By Industry Benchmarking
2021 Cybersecurity Threat Trends
Mandiant Security Effectiveness Report: DEEP DIVE INTO CYBER REALITY
Back Up Your Data to Get It Back From A Cyber Attack

Today’s accelerated technology trends are powering unprecedented business transformation. But they’re also introducing an overwhelming amount of security risk. Hackers use a wide range of tools and methods to gain access to your data—from social engineering and phishing scams to ransomware attacks and exploiting systems vulnerabilities. With virtually all personal and business data stored on internet-connected platforms, targeting businesses has become a gold mine for bad actors. To ensure the best chance of business continuity following any compromising cyber event, strategically backing up your data is one of the most foundational best practices you should include in your layered security checklist.
Business-Critical Backup and Recovery, Without A Plan
Cybersecurity professionals agree pretty much universally that, it’s not a matter of whether businesses will encounter an attack, but when. Trying to execute every-day business functions, without access to data, is like trying to drive a car without the tires—basically, inoperable. The very purpose of an holistic security strategy is to minimize as many gateways available to threat vectors as possible; local (on-prem locations), geographical distribution (networked systems) and cloud backups (primary or redundant data storage) are fundamental first steps in a layered approach to protecting your data.
Unfortunately, employing a data backup strategy isn’t as universally agreed upon. If that sounds contradictory, well, it is. In fact, even many IT professionals generally view backups as an insurance against the potential for an attack verses a priority to combat attacks. But consider this common scenario: a company has recognized the importance of backing up data and engages IT to deploy it. A random device is selected and turned on in a single location, but never tested, runs on subpar hardware, and has no particular defined parameters. This approach has a very different outcome during recovery from a cyber attack than a strategic data backup solution.
Business Continuity Predicated on Data Recovery
If you’re employing a set-it-and-forget-it backup strategy, you’re in for a rude awakening when an incident occurs. Waiting until you need your backups is, arguably, the worst time to wonder how many copies of your data are available and where and how they’re stored. During an incident, time is critical; downtime adds up quickly and can be extremely costly to your customers, your reputation, and your bottom line. Some businesses simply can’t recover; they go out of business. For a significant outage, you need to be able to act fast and be responsive. If you, or your solution provider don’t know what you don’t have, you’re looking at a substantial amount of downtime, and mounting associated recovery costs, as you work it out.
Making Cybersecurity A Priority with Data Backup
Companies are best positioned to assure business continuity if each of these steps have preceded an incident:
- Security-minded culture: user behaviors and policies awareness; ongoing compliance reinforcement
- Preventative measures: annual third-party security assessment to document vulnerabilities in the security controls, along with correction recommendations; firewalls and backup strategy functioning as intended; allow listings and access controls implemented; timely patching; audits, testing, monitoring, and spot checks; and fire drills to ensure everything is documented and security settings haven’t changed
- On-call service in place: 24/7/365 fully-staffed, live helpdesk of experienced, certified engineers with a 15-minute disaster response time
Off-loading some of the routine tasks associated with cyber hygiene like software updates, patching, testing, and backups to an MSP like Path Forward IT is an investment in your overall security plan. This simple step enables a service provider, with end-to-end data protection solutions, to get to know your systems environment intimately, enabling expert counsel for when you need to make operational changes that impact IT, are thinking about a purchase decision, or encounter an attack or natural disaster.
Backup Options Matter
Of course, you never want to get to recovery mode, but when you do, the quality of your backups will be very important. The best mitigation for destructive cyber-attacks is having rock-solid backups. However, with the advent of affiliate ransomware, attackers will now go after any accessible backups too. This makes a secure cloud-based backup solution a good choice—one that uses authentication that requires a unique set of complex credentials for access (does not overlap with workstation, server, or domain credentials) and does not require physical servers in the event of a disaster. What makes Cohesity enterprise-class backup solutions the preferred choice of so many enterprises worldwide are the expanse of options available to prepare your organization for a variety of data compromises. Cohesity provides a secondary repository with immutability, for offsite storage, ransomware early detection, and other advanced security features, along with a team behind it, monitoring and testing everything daily to ensure its efficacy.
The benefits of backup options become crystallized during a recovery operation. Customized data protection and recovery solutions provider, Path Forward IT, points to less production impact and downtime in general, rapid speed to restore, massive data storage of up to 35 PiB (pebibytes), granularity, and the flexibility to scale and customize the solution to fit customer needs.
Backup As Last Line of Defense
A layered security strategy improves your chances of stopping threats from penetrating your environment. But as new technologies develop and threat actors mature in finding ways to exploit them, strategically backing up your data can mean the difference between business devastation and a quickly-contained service interruption.
“If you put a key under the mat for the cops, a burglar can find it, too. Criminals are using every technology tool at their disposal to hack into people’s accounts. If they know there’s a key hidden somewhere, they won’t stop until they find it.”—Tim Cook, CEO, Apple Inc.
To learn more, request a consultation with Path Forward IT.
—
Resources
How Well Do You Monitor Access to Company Information?

Whether or not an employee can see or open a particular folder or application should not be arbitrary. Being intentional about access controls is vital for compliance and security. This introduction to access controls lays out the key steps and considerations for reducing risk and securing your data.
An Introduction to Access Controls
You take security seriously. You lock your front door. Your phone password is 12 digits long.
Now it’s time to concentrate that focus inside your organization. Just as you protect your information from outsiders, you need to be sure it’s safe inside too.
Access controls have a simple but critical job. They control who has access to your information, what that user can access, and what that user can do. It’s a critical component of your cybersecurity strategy.
Who Approves Payroll?
Consider payroll.
It’s an intuitive example. You don’t let everyone in the company cut their own paychecks. Your payroll system is only accessible by certain staff. The payroll staff is responsible for specific tasks, like how your payroll accountant can enter timecards but needs a manager to approve pay raises. And nobody gets paid until your HR Director signs off on the pay run.
Your controls might look a little different, but the goals are the same:
- Users have access to what they need.
- Users can only do what they’re allowed to do.
- Checks and balances help to detect and prevent problems. This includes separation of duties and periodic user access audits.
Where to start
Any organization starts with the same fundamental steps no matter what the business looks like, how many people it employs, or what kind of information it protects. A compliance consultation is a great way to map out your access controls.
1) Decide WHAT you need to protect.
Create (or update) your policy to define your security requirements. Keep it high level. What kind of functions need extra security? What are you willing to share with outsiders, and what stays in-house?
2) Decide HOW you’ll protect it.
Who decides what information needs to be protected? Who’s responsible for implementing and maintaining access controls? In general, what kind of access controls will you need? Who approves changes to user access, and how do you document it? What happens if someone violates the policy?
3) Determine WHO needs access to what.
Access is determined by the role and what each role requires access to in order to do the job. This includes access to software, shared drives, and even parts of your facilities. You may need to do some fieldwork to find out exactly where duties overlap.
4) Verify whether your users have the right access.
Many software systems include standard reports and other security management features. Do it again next quarter. And next year. And so on. Consider engaging an IT consultant to help confirm your controls work correctly.
5) Don’t forget about vendors and partners.
Can anyone outside of your organization access your files? If a vendor has excessive access, would you even know it before they put your entire organization at risk?
Pro Tip: Take advantage of read-only and other restricted access levels when possible. For example, your payroll accountant might need read-only access to your production scheduling system to validate overtime. Or a hospital’s CFO might need to run reports from the medical records system, but he or she shouldn’t be able to edit patient charts.
The Risks of Not Having Access Controls
Auditing user access is a pain in the neck. But the risks of ignoring access controls are much worse.
1) Compliance nightmares.
Can the same person authorize a payment, cut the check, and reconcile the bank statement? It’s not just a good idea to have internal controls; in many cases, it’s the law.
2) A hacker’s dream.
The more access you give to a single employee, the bigger the risk if that person’s account is hacked. For example, what could a hacker do with your CEO’s login credentials?
3) Escalating access.
It’s easy to forget to change access when someone changes roles. If our hypothetical payroll accountant gets a promotion, will he or she then be able to approve his or her own pay raises?
4) Leaving the door open for terminated employees.
You wouldn’t let a terminated employee keep a security badge. Don’t let them perpetuate a major HIPAA breach.
5) The domino effect.
If a vendor or partner gets hacked, you’re the next target. Don’t let your HVAC vendor cost you $162 million in data breach cleanup.
As I said, an access control audit looks a lot better after you consider the alternatives.
Last Pro Tip: You don’t have to do it alone. Start with your accounting and legal partners to learn more about what tools they can offer.
You can also contact us directly if you have any questions or if you would like to learn more. We’re always happy to talk shop.
5 Tips for Keeping Data Protected

COVID-19 has changed the way we live and work, with many of us balancing remote work with time in the traditional office. Remember that HIPAA and other regulations still apply. Here are five fundamentals for protecting yourself—and your patients—when you’re working at home.
These are geared for our colleagues in the healthcare industry, but we believe that the principles apply to anyone working online.
1. Check with your IT department first.
If you’re on a company-owned device, don’t download or install software without checking with IT first.
Take extra care when you see notifications for system updates. A serious attack earlier this year pretended to be a Microsoft Office 365 update and tricked users around the world into giving up their login credentials with a fake update warning. Training is available to help detect phishing attacks like this.
The best idea is to always check with your IT team before you update. IT departments can put measures in place that restrict some downloads and help protect the company.
If you’re on the IT team, consider how you communicate your patch and update schedule to end-users. Do they know what to do if they get a notification, whether that notification is real or malicious?
2. Public WiFi is NOT secure.
Avoid WiFi that you would get at an airport, hotel, or restaurant — these locations are notorious for security issues. Hackers can use simple devices to intercept anything you send over a compromised network.
Never access PHI, including medical records, over a public or other unsecured WiFi. Period. Don’t use unsecured WiFi to access your online banking or anything else you need to keep safe.
Talk to your IT team about ways to stay safe and encrypted. That way, you can be confident that your personal information and sensitive work are protected.
3. Save sensitive information carefully.
Whether you’re using a company-owned device or your own device, never save any Protected Health Information on your desktop or C drive. Any data covered by HIPAA must remain secure. Don’t put yourself – or your patients—at risk.
Make sure you understand and follow your organization’s policy for storing and sharing information. It’s a good idea to check your desktop, C drive periodically, and download folder to make sure you’re in the clear.
If you’re having trouble convincing your colleagues to take this seriously, ask them to Google “doctor lost laptop.”
4. Be vigilant.
Hackers know the challenges of working remotely, and they’re taking advantage of it to attack. Healthcare is especially vulnerable because our data is valuable, and our work is critical.
This isn’t intended to scare you. Instead, it’s a reminder that we, as an industry, need to be vigilant. Your organizational risk assessment must recognize the increased threat to your people, systems, and data. When was the last time you updated your information security training materials?
5. Ask for help.
Remember that you’re not in this alone. Reach out to your colleagues and especially the IT department when you have questions or unsure if an email is legitimate.
You can also reach out to Path Forward with questions, comments, or to brag about how you foiled a cyberattack. We look forward to hearing from you.
